Hierarchy security has a bit unexpected side-effect. In theory, it is supposed to give managers access to the records assigned to their subordinates – I am assuming the idea there was to bypass role security and to quickly give managers access to that data.
But what if we had a record assigned to a user, and what if that user did not have any permissions (not even “read”) for the entity? Would a manager of that user be able to see such record?
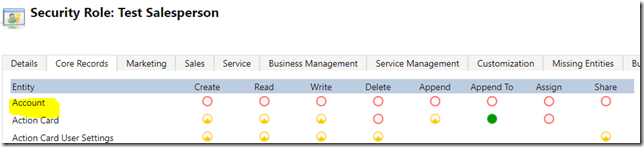
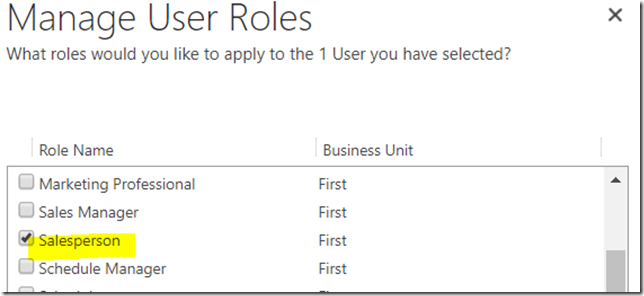
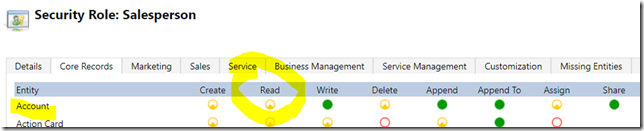
As in the example below, my “Test Sales Person” role does not give access to the account entity:
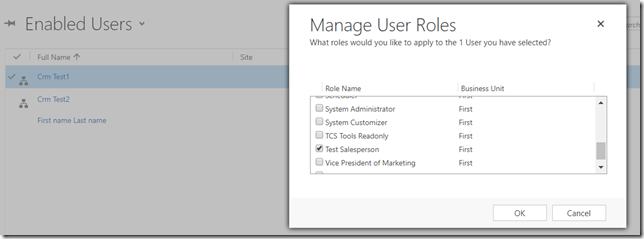
And it’s the only role assigned to the Crm Test1 user:
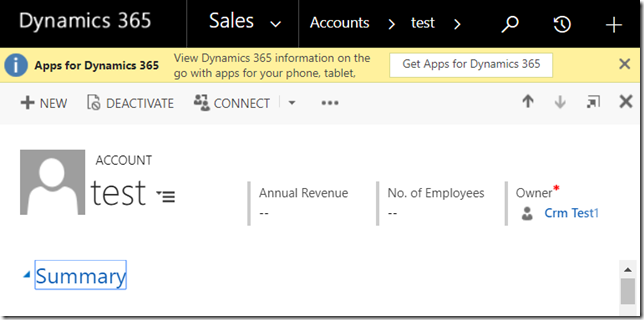
Now, there is an account record assigned to Crm Test1:
It is a “historical” record stuck with the user from the times that user had access to the account entity.
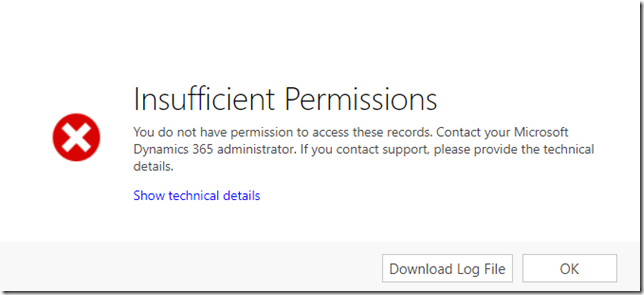
Right now, though, if the CrmTest1 user tried to open that account, here is what they would see:
And, in the log file, there would be this error message:
<Message>Principal user (Id=165066b2-a658-e811-80be-00155d00c103, type=8) is missing prvReadAccount privilege (Id=886b280c-6396-4d56-a0a3-2c1b0a50ceb0)</Message>
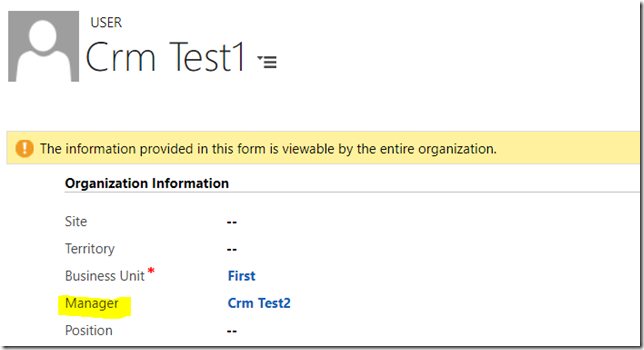
However, CrmTest1 has a manager:
That manager has a slightly customized Sales Person role:
Normally, that particular manager would only see account records assigned to themselves.
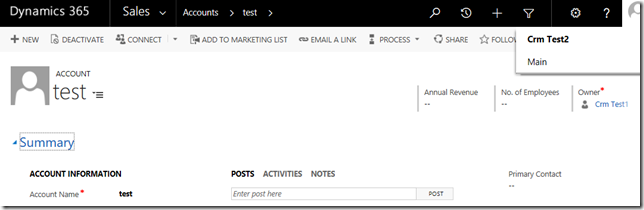
However, because of the hierarchy security, our manager user can see the records assigned to his/her subordinates:
In other words, hierarchy security ignores “subordinate user” permissions – it’s just looking at the ownership when deciding if the manager can see those records or not. And the user can loose permissions as a result of role change or, sometimes, as a result of business unit change (since that’s when all user roles will be removed automatically).