The whole reason I started to look into the details of OAuth in the previous post is that I really wanted to see how to set up external identity providers for the portals.
There are some great blog posts out there which are describing the process in a step-by-step kind of way with all the necessary screenshots:
https://readyxrm.blog/2019/07/24/configure-azure-ad-b2c-for-powerapps-portals/
There is a documentation page as well which can walk you over pretty much the same steps:
https://docs.microsoft.com/en-us/powerapps/maker/portals/configure/azure-ad-b2c
What I was looking for is a bit better understanding of what’s happening behind the scene, though.
As a result, I think there are three items to discuss in this post:
- OpenID Connect
- Azure AD B2C
- Setting up the portal to work with Azure AD B2C
But, again, if you have not looked at the OAuth, or if the term “implicit flow” still sounds too alien to you, have a look at the previous post and all the references there.
Because here is how it all works:
- We can configure portals to use Azure AD B2C as an identity provider
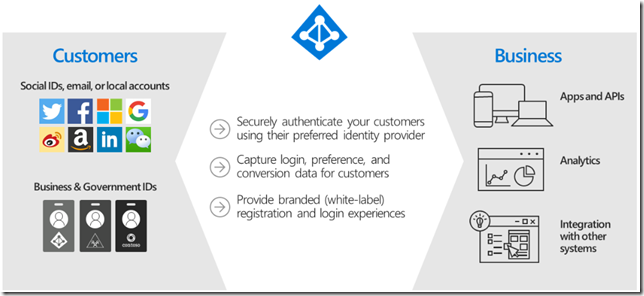
- Azure Active Directory B2C is a service from Microsoft that enables external customer sign-ins through local credentials and federation with various common social identity providers
- Portals do support Open ID Connect, Azure AD B2C does support Open ID Connect… so there you have it: one can work with the other using Open ID Connect
What is Open ID Connect, though? It’s an extension of OAuth to start with, so we are still talking about all those client id-s and implicit/code flows. However, when utilizing Open ID Connect, we can get not only the authorization token, but, also, the so-called id_token. Which will actually represent user identity – there is a nice walkthrough in the post below if you are interested:
https://connect2id.com/learn/openid-connect
Azure AD B2C supports Open ID Connect: https://docs.microsoft.com/en-us/azure/active-directory-b2c/active-directory-b2c-reference-oidc
Portals support Open ID Connect and can be configured to work with Azure AD B2C: https://docs.microsoft.com/en-us/powerapps/maker/portals/configure/azure-ad-b2c
What’s interesting is that Azure AD B2C can also work as a “proxy” between the portal and external identity providers:
https://docs.microsoft.com/en-us/azure/active-directory-b2c/active-directory-b2c-overview
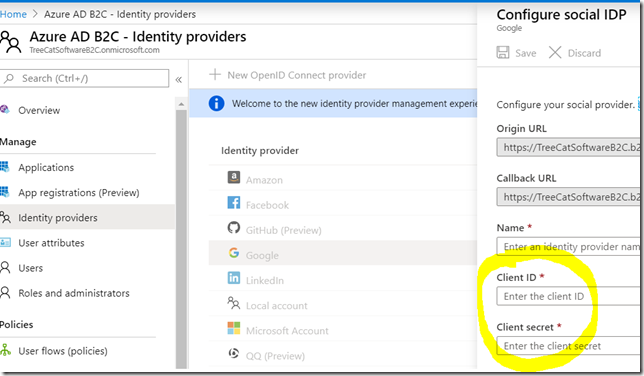
Even though those external identity providers have to be configured in your instance of Azure AD B2C, since, from the external identity provider standpoint, your users would have to authorize Azure AD B2C to access user identity information. So, for example, for the identity providers which are relying on OAuth, you’d have to go over the regular client registration steps to get client id & client secret so you could set up those providers in Azure AD B2C:
As I mentioned before, Azure AD B2C will work as a “proxy” in that sense. The portal will ask Azure AD B2C for the user identity, but Azure AD B2C will offer your users an option to authenticate through a configured external provider (and the portal does not need to even know about it).
Which may give you the benefit of single sign-on between the portal and other applications using Azure AD B2C(no matter if, ultimately, your users are using google/facebook/twitter/etc identity).
As a side note, what if you did not have Azure AD B2C and still wanted to use Google for portal authentication, for example? That would still be doable:
https://docs.microsoft.com/en-us/powerapps/maker/portals/configure/configure-oauth2-settings
With all the above, it should be easier now to answer some of the questions about all this set up process, such as:
Why do we need to register an app (OAuth client) in Azure AD B2C for the portal?
That’s simply because it’s OAuth, and we need a client id to make requests to the OAuth server
Why do we need to register an app (OAuth client) in Google if we wanted to add google identity provider to Azure AD B2C?
That’s because Azure AD B2C will be using OAuth to request authorization from the google OAuth servers for the usage of google profile API-s etc
Why would we choose Azure AD B2C over other external identity providers?
Essentially, this is because we’d be outsourcing identity management to a separate service that has a bunch of useful features available “out of the box”: https://docs.microsoft.com/en-us/azure/active-directory-b2c/technical-overview
As for setting up your portal to work with Azure AD B2C, I’ll just refer you to the same two pages I mentioned earlier in this post:
https://readyxrm.blog/2019/07/24/configure-azure-ad-b2c-for-powerapps-portals/
https://docs.microsoft.com/en-us/powerapps/maker/portals/configure/azure-ad-b2c
PS. There is a continuation to this post here – you will find additional details on how to set up the portals with Azure AD B2C, and, yet, how to enable additional external identity providers through Azure AD B2C: https://www.itaintboring.com/powerapps/power-app-portals-and-multiple-external-identities/
Have fun!