Earlier this month I was thinking of a way to use “on demand” licensing with Power Platform (including Power Pages) for a “micro business” company, and, although it’s probably arguable what makes sense and what’s not, but one of the things I wanted to figure out is whether it would be possible to lock down Power Pages site in such a way that unauthorized users just would not be able to reach it at all. Eventually, that might allow me to set up the whole process like this:
- Whenever someone goes to the portal, they’d need to use an address that’s different from the actual Power Pages site address
- They’d be asked to sign in with Azure B2C first
- Once they have signed in, there would be an additional check to see whether that user account has been authorized to access the portal
- If not, they’d be forwarded to some other (non-portal) page
- If yes, they’d be allowed to proceed to the portal (still using my own domain name which is different from the actual Power Pages domain name)
Up until the last step above, that hypothetical user wouldn’t be accessing Power Pages site at all, but, even then, they’d be accessing Power Pages site through the reverse proxy and the actual Power Pages site address wouldn’t be exposed at any time. So, ultimately, on the pay as you go model, only authenticated and authorized users would be accessing the portal.
Either way, I’ll need to think through those usage scenarios, but, from the technical perspective, it seems I do have a working prototype now. Here is a diagram illustrating my current configuration:
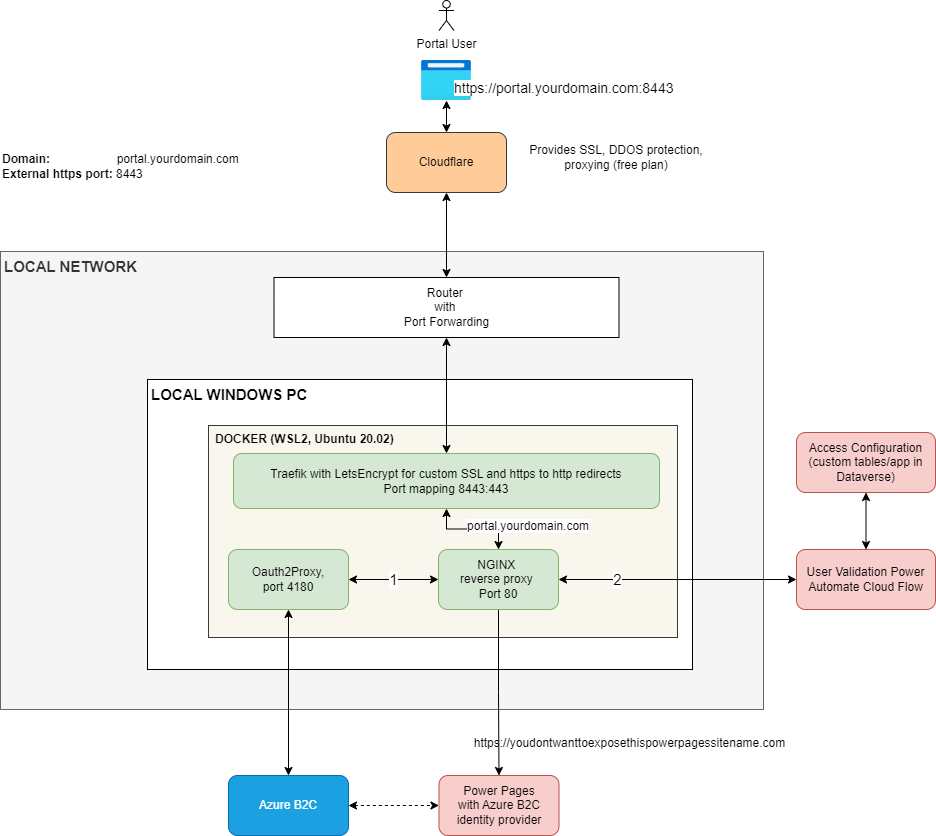
It’ll take some time to explain this step by step, so I’m not going to do it right away (after all, there must be something to blog about, can’t just give it all away in a single post 😁).
Here is a git repo with docker compose, nginx, and traefik configuration BUT it’s currently missing some key files (need to clean it up – there are client id-s, secrets, etc):
https://github.com/ashlega/ITAPowerPlatformExtensions/tree/main/ProxiedPortal
On top of that, there are a couple of recordings below.
In the first video, you’ll see what it looks like when I’m trying to access the portal using a gmail account that has not been authorized:
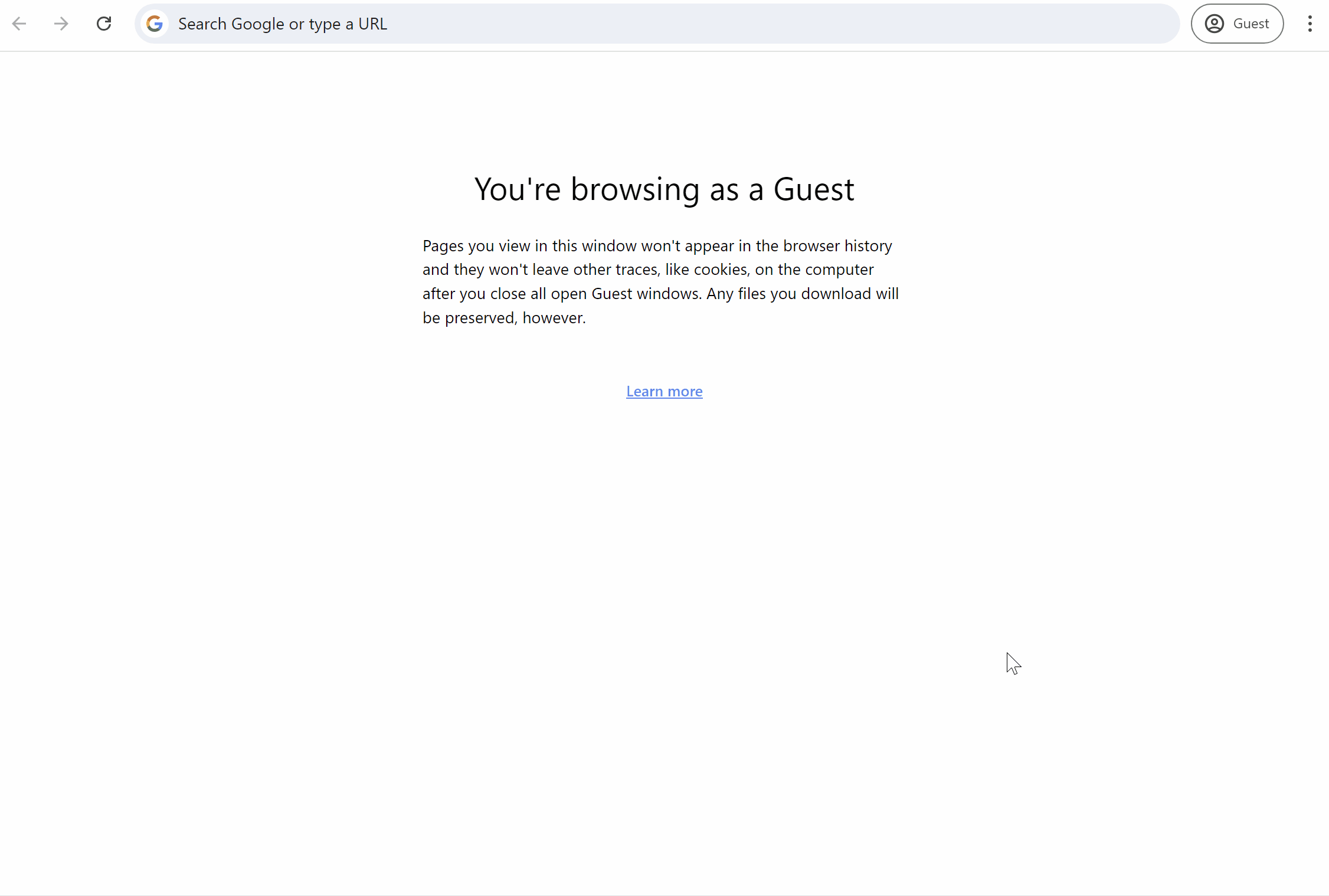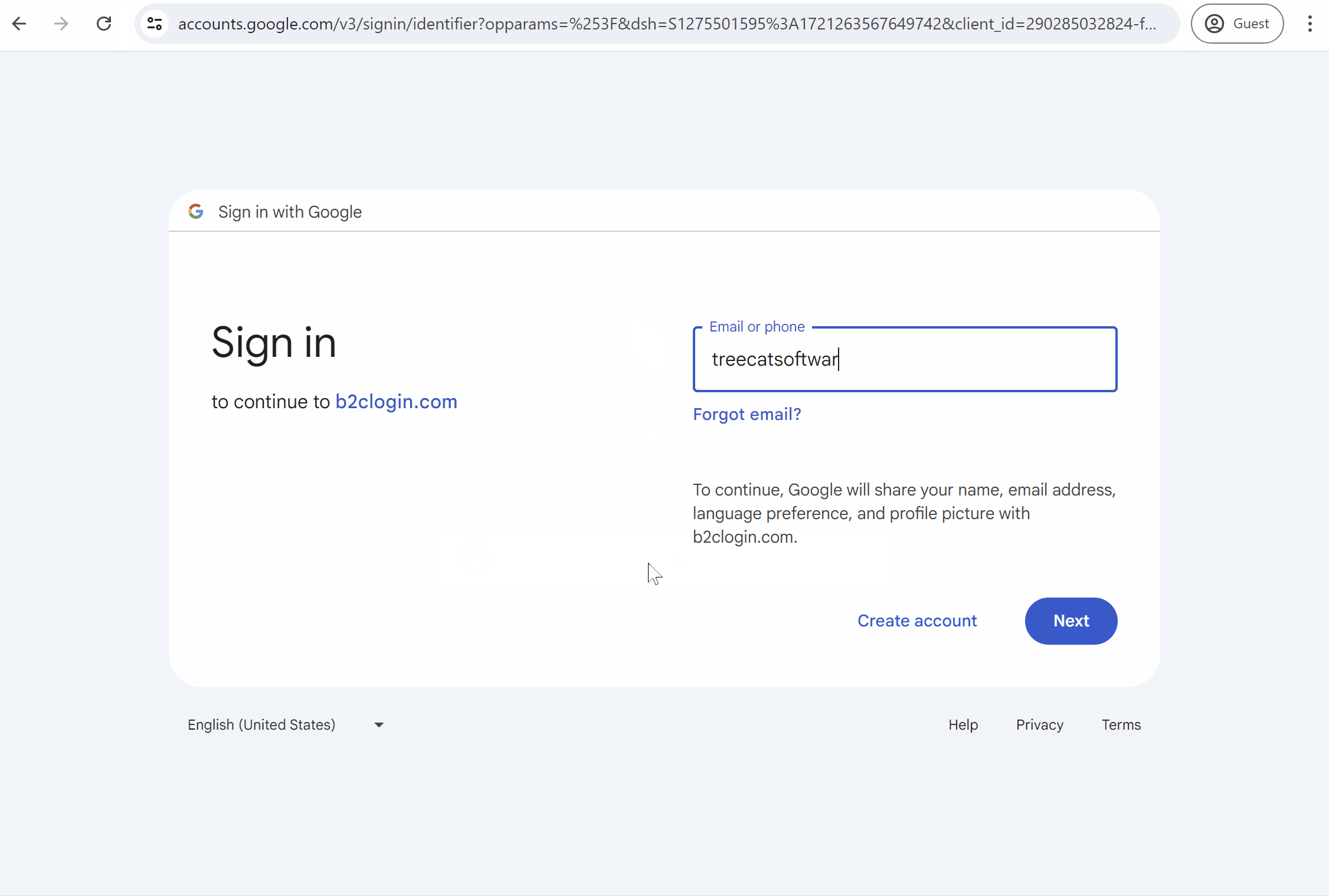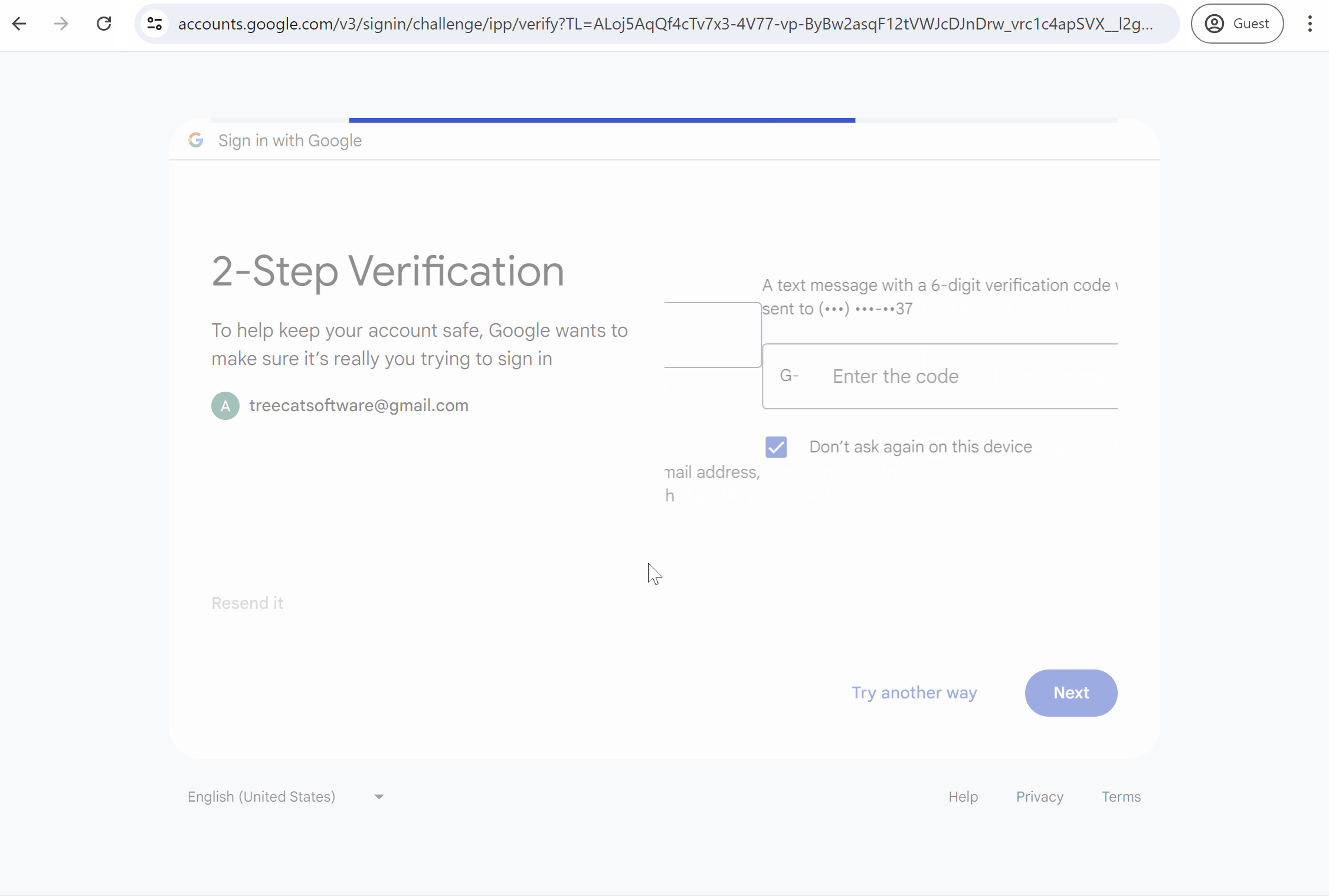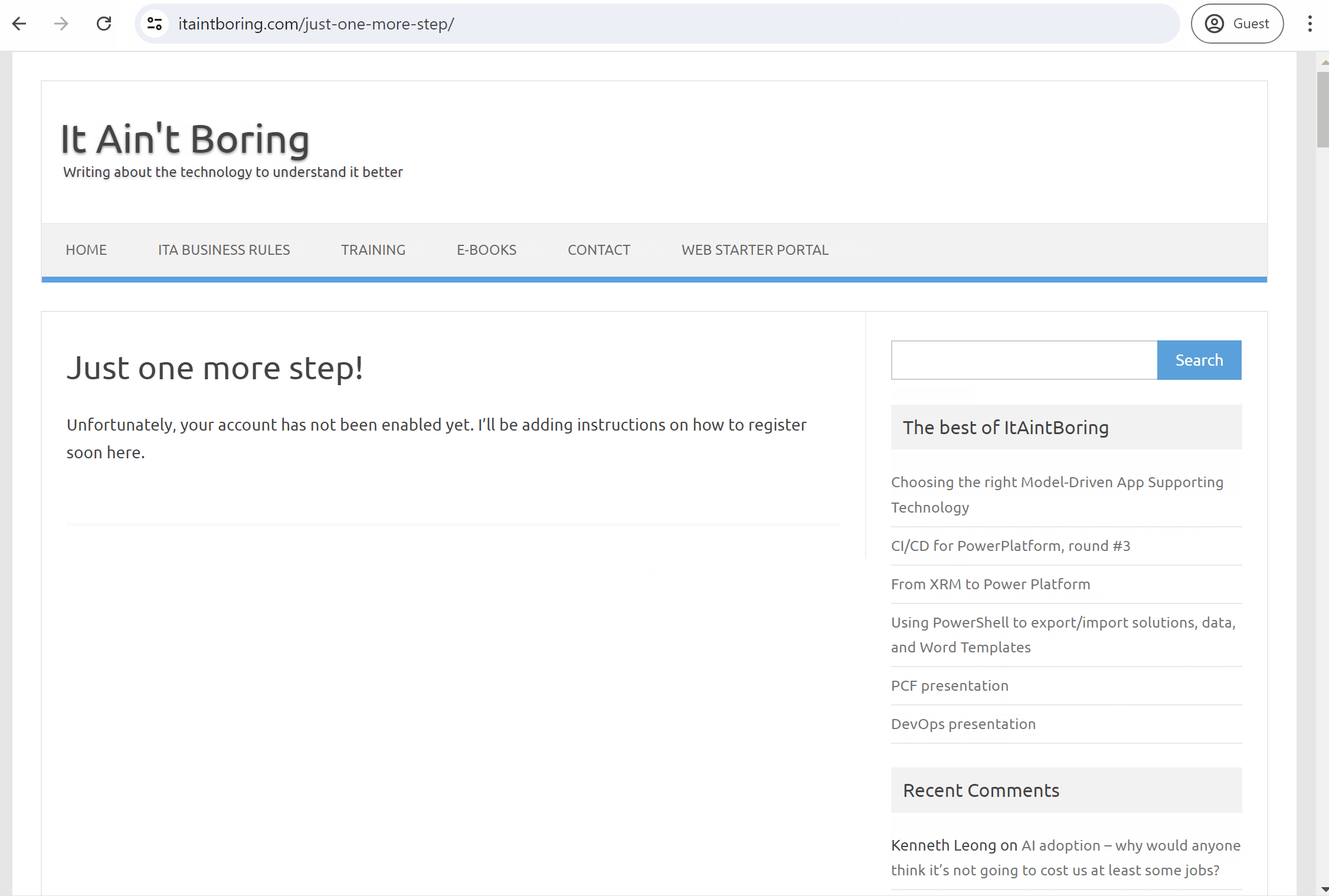
And, in the second one, you’ll see how it works for a user who has already been authorized to use the portal:
If you wanted to give it a try, continue to the next part